blockchain for noobs
by chiarascuro
This article is about 2000 words, so feel free to skip around.
contents
"A blockchain is a digital double-entry ledger in which transaction histories are securely and permanently recorded using cryptography and consensus," says your friend who's really into blockchain stuff.
Yeah, I tried once to explain it to someone that way, and it didn't help them understand the blockchain at all. So I wrote this article.
If you're new to blockchain technology, this is for you.
Many sources call it a decentralized ledger, and in many cases it is. But a ledger built on blockchain technology can also be stored in a centralized way. And control over the record-keeping can be centralized, too.
It’s called a blockchain because each block contains transaction data and is linked to the other blocks by cryptographic hashes -- encryption that ensures nothing is fiddled with.
What's in a block?
You can think of a block as a container for transaction details.
For example, each block in a proof-of-work blockchain like Bitcoin or Ethereum contains:
- Hash of the data from the previous block
- Timestamp
- Database of recorded transactions (from, to, and amount)
- Nonce (mining difficulty score)
The first block minted onto a blockchain is called the genesis block. When it's full of transaction data, a second block must be created. And a third, and so on.
But who's making sure these transactions are 1. real, and 2. recorded onto the blockchain? And who's making sure those people do what they're supposed to instead of intercepting the transactions and stealing all the crypto?
Blockchain security relies on hashing, public key cryptography, and consensus
It’s not easy for anyone to successfully attack a blockchain. This is because blockchain technology operates with other technologies and protocols to validate blocks:
- Hash functions. A hash algorithm scrambles data into a string of alphanumeric characters of a specific length.
- Public key cryptography. A public key is paired with a private key. The public key encrypts data, and only its corresponding private key can decrypt that data.
- Consensus mechanism. Each block must be validated before it’s added to the chain. Proof-of-work and proof-of-stake are the most common ways to reach consensus.
Depending on what kind of blockchain it is, it might also use:
- Tokenization. The creation of a digital representation of an asset. This could mean a fungible token or an NFT (non-fungible token).
- Smart contracts. Pieces of code that verify and legitimize an agreement between two parties by virtue of the execution of the code itself.
how a cryptographic hash works
A hashing algorithm works kind of like the Play-Doh Barber Shop.
Imagine mashing three different colors of Play-Doh into a ball and put it through the Barber Shop a few times.
A hashing algorithm works the same way when it encrypts data, only it does a much better job of mixing the colors. Your public key takes a piece of data and smooshes it together until it bears no resemblance to the original data.
Only the private key in the pair can sort it out.
try hashing yourself
SHA256, the most commonly-used hash algorithm, outputs a string 256 characters long no matter the size of the data. Try the SHA256 hash generator yourself and see what it does.
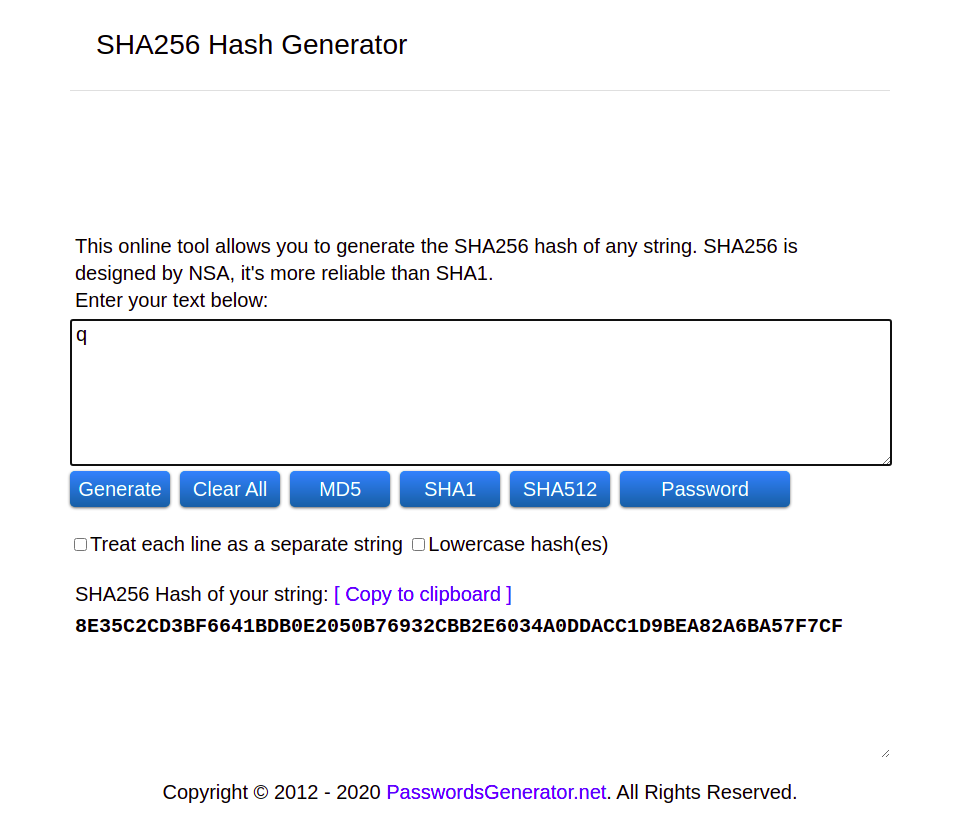
Here I’ve typed the lowercase letter q. The algorithm hashes it into a 256-character string.
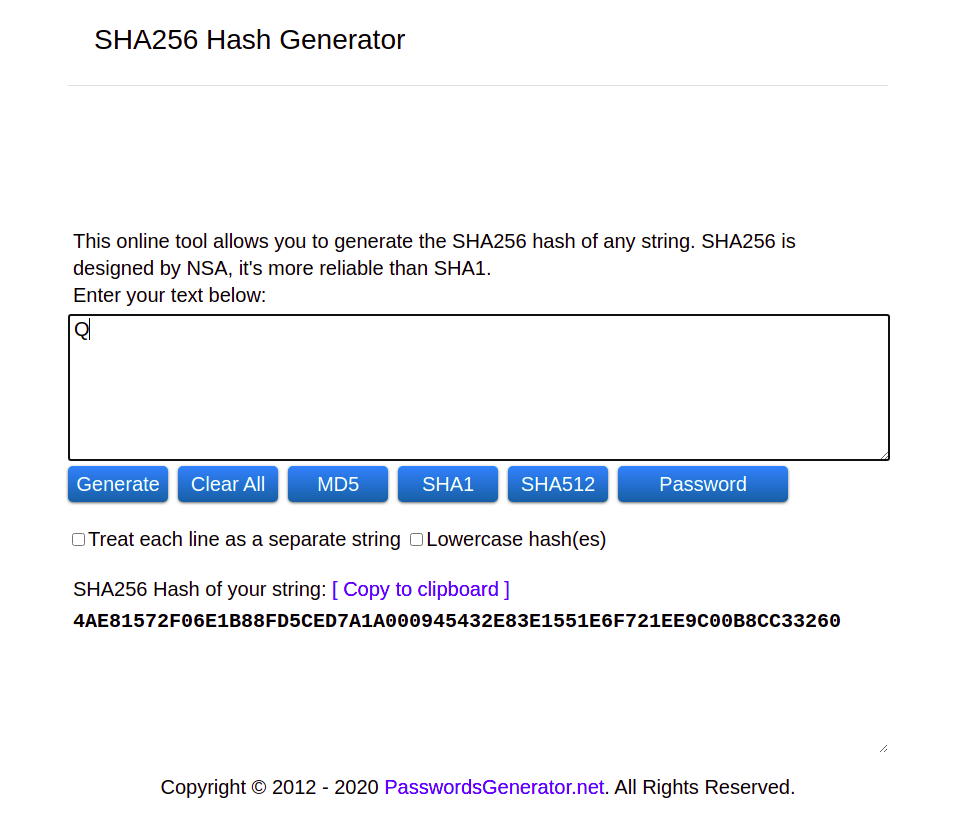
See what it does when I replace the lowercase q with an uppercase Q? The same letter, only capitalized, results in a totally different hash.
The hash will output a drastically different string even if only one character is changed. Why? To make it more obvious if even one bit of data has been tampered with.
It doesn’t matter how many characters, bytes, or gigabytes the original data contains. It doesn’t matter if that data is a text document, image, audio clip, or video.
The output will always be a 256-character hash that’s radically different from a hash generated by similar input.
hashing the hashes
When the genesis block in a blockchain is minted, all of its transaction data is hashed and recorded into the second block. When the third block is created, it contains a hash of all the data from the second block, which contains a hash from the first block. That way, no matter how many blocks are on the chain, the data from each previous block is always there.
Hashing all that data together in a sequential way helps make it possible to verify the authenticity of the data.
If data in one block is tampered with, it drastically changes the hash. Since that block’s hash is hashed with all the subsequent blocks, it causes a domino effect of changed hashes that alerts the system that someone’s trying to do something they shouldn’t.
how public key cryptography works
Public and private keys are created together in pairs. They can only work with each other. Your public key encrypts data so you can send it without anyone being able to interpret or use it.
No one can see the real contents of the encrypted data without your private key. Doesn’t matter if they have their own private key. Their private key can’t decrypt data that was encrypted by your public key. Only your private key can do that.
This is not to be confused with your wallet password or seed phrase. A seed phrase is generated as a way of encrypting your private key in a human-readable way. It’s a randomly-generated series of words you use to recover your digital wallet.
Anyone who has the seed phrase to your wallet has control of the private keys. They can make transactions, change your password, and steal your wallet. So don’t ever share it with anyone.
how concensus works
Transactions have to be verified for each block to be validated. In a decentralized system, certain computers on the network (called nodes) do this job.
Nodes communicate with each other to validate the blockchain and store local copies of it. This distribution ensures that, if one or more nodes fail, thousands of other nodes in many geographic locations still have copies.
As long as there is at least one node that contains a local copy of the entire blockchain, the ledger (and therefore the network) is still intact.
A node operator (sometimes called a stake pool operator or validator) verifies data and creates blocks using software. Bitcoin miners use enormously powerful computers called mining rigs.
There are different ways to reach consensus. Next, I’ll talk about proof-of-work, proof-of-stake, and delegated proof-of-stake.
proof-of-work consensus
Nodes in a proof-of-work system like Bitcoin are operated by miners. A miner is a person or entity who validates transactions on this type of blockchain. They “mine” for a nonce with a lower difficulty than what’s determined by the system.
That nonce is called the “golden nonce” and the miner who finds it first is allowed to create the next block and receives a financial reward.
But to do that, they must compare many metric f*ck tons of cryptographic hashes to find one that works and is below the difficulty established by the nonce. The larger the network, the more computing power (and electricity) it takes to mine.
The amount of work it takes to validate a block is considered proof that the data is valid. If any data is tampered with, the block is immediately invalidated and the miner has to start all over.
To get the reward, they have to compete against many other miners to validate blocks with the correct data. So proof-of-work does a great job of ensuring correct transactions. But there are a couple of issues with it.
It’s not only slow, proof-of-work mining uses a lot of energy. And because the electric company isn’t as generous as the blockchain community, it’s expensive.
So proof-of-stake was created as an alternative.
proof-of-stake consensus
Instead of requiring nodes to validate by brute force computing power, proof-of-stake grants nodes permission to create blocks based on the amount of stake they own in the network’s native currency.
That means node operators that own the most tokens get to create blocks and receive the block awards. If you operate a node on such a network, your chances of creating a block increase the more currency you’ve staked.
Staking simply means that you dedicate currency to be held in the network. This supports the development of the network and its ecosystem, which is what makes a blockchain network successful. Staking means you get to participate in block creation and get a percentage of the block rewards.
It also means you get to participate in the governance of the blockchain by voting, which is pretty damn cool.
Because nodes can create blocks based on what they own rather than computation, PoS networks are a lot faster and use much less energy.
But they present an older and even more familiar problem. People who have the most money can buy the most native currency and hoard block rewards. Which means the rest of us don’t get a chance to create blocks at all.
So what’s to keep some billionaire or monolithic corporation from buying up and staking the lion’s share of crypto so they can have a monopoly?
Nothing.
That’s where delegated proof-of-stake comes in.
delegated proof-of-stake consensus
Delegated proof-of-stake addresses the “rich get richer” problem by allowing participants who own small amounts of currency to delegate it to a node operator. In other words, pooling their resources to increase their chances of creating blocks and getting rewards.
When the node operator creates a block, the block reward is shared with everyone else in the pool based on the percentage of currency they’ve staked in it.
Cardano is a delegated proof-of-stake blockchain network. If you own Ada (Cardano’s native cryptocurrency) you can choose a pool to stake it with. Even if you only own a tiny bit. And if your pool’s node is granted the opportunity to create a block, you and everyone else who has staked in that pool profit from it.
The reward is added to your staked amount by default. If you want, you can reallocate it or withdraw it. But you could also leave it staked and reap greater rewards later.
Now you know what a blockchain is, the basics of how it works, and a few other things. What were they?
remember ...
A blockchain is a digital ledger of transactions secured by cryptography and consensus. It may be stored and/or “governed” in a centralized or decentralized way.
Hashing functions and public-key cryptography work together to verify and record transactions in a tamper-resistant way:
- Hashing algorithm. Turns any piece of data into a 256-character string.
- Public/private key pair. Gives you a public address where you can safely receive data and a private key for you to unlock it with.
Hashing is also used to record and consolidate each block’s transaction history into that of the next block. This is what makes it easy to detect if someone has tried to mess with it.
A consensus must be reached about the validity of each transaction before it can be recorded on the blockchain. Proof-of-work and proof-of-stake are the most common consensus mechanisms, but there are new ones emerging as well.
That's a lot. But with some education, you'll be navigating the cryptoverse like a tween getting around parental controls. Welcome to Web3. Be safe out there.
resources
This wouldn't be much of an explainer article without a list of more things to eat away at your time. But if you're going to be looking at your phone anyway, you might as well be learning something.
So here are some things you'll want to check out if you want to learn more about crypto, DeFi, or blockchain technology. Especially if you're hanging with us here on Cardano.
These are all from the library of The Alexandria Project.
in English
- Bitcoin: A Peer-to-Peer Electronic Cash System. Bitcoin is the world's first cryptocurrency, and this paper written by the fake person Satoshi Nakamoto explains the need for it.
- THIS CRAZY KITCHEN: Workshops (Volume 1). This token is actually a legendary series of six workshops created by ThisCrazyLife and CardanoNoodz. Everything you need to know to mint NFTs and FTs on Cardano!
- The Ouroboros Papers. A series of papers about Ouroboros, Cardano's blockchain protocol.
- Charles Hoskinson "Whiteboard: DApps and Development" (2022). Just what it sounds like. Charles Hoskinson, founder of Cardano, talking about building dApps on it.
- Learn Cardano Podcast - Episode 33. Learn about DAOs, security and utility tokens.
in Spanish
- DeFi-nitivamente Educativo. A series of DeFi podcasts about decentralized finance.
Hey - if you find these useful, delegate to Infinite Pool (INFI), which supports the Alexandria Project and its mission to disseminate human knowledge. Infinite Pool was founded by Cardano NFT creators CardanoNoodz and Fractal Fuzion.

about chiarascuro
chiarascuro is an analog painter, digital illustrator, writer, editor, and HTML/CSS dabbler. She creates abstract art, portraits, and illustrations of robots doing human things. (She is not a robot. If you peel away her human face, there is definitely not a metal skull with glowing red eyes underneath.)
Check out her other work and reach out to her on Twitter.
